Pentester Academy Course Review - Attacking and Defending Active Directory
Apr 27, 2019 · 5 minute readIntroduction
I recently had the pleasure of purchasing and successfully completing Pentester Academy’s Attacking and Defending Active Directory Course. The main objective of the course is to provide a high quality learning platform for security professionals to understand, analyze and practice threats and attacks in a modern Active Directory environment. The course author is Nikhil Mittal who is a seasoned AD penetration tester and researcher. The course’s overall approach is to teach how to perform a Red Team assessment with an assume breach mentality.
Here’s the course introduction video.
Also a high level overview of the labs.
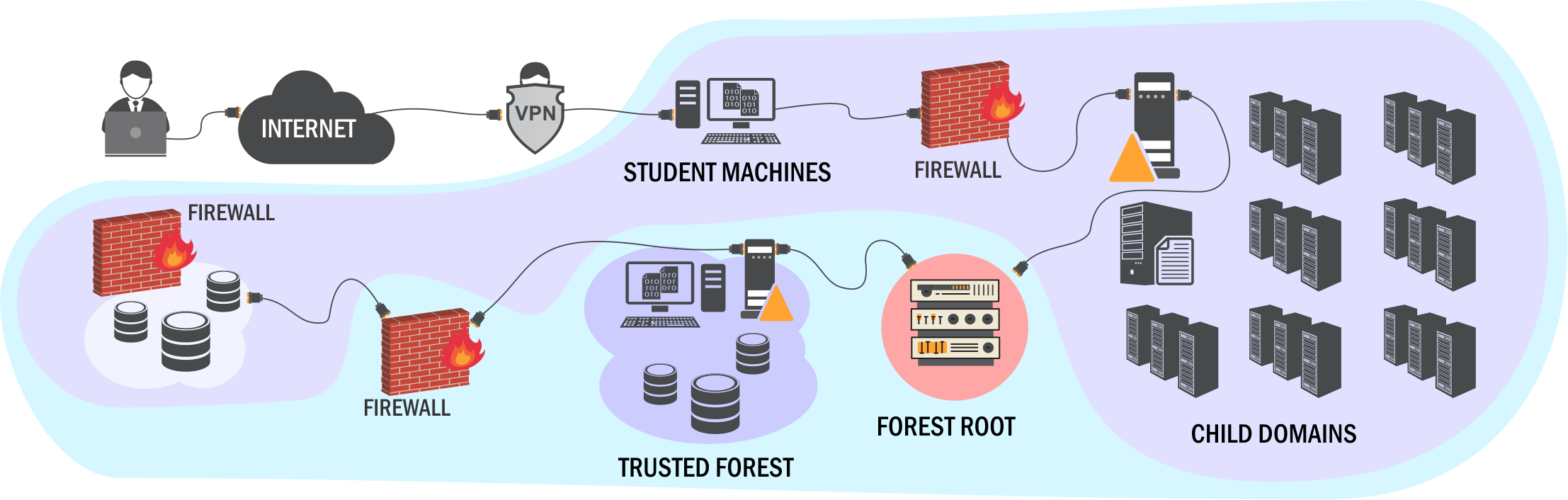
Motivations
I initially bought this course based on a great learning experience I already had with the author’s PowerShell for Pentesters course. I love doing training that requires I keep my hands-on technical skills sharp. The low cost of the labs compared to the value returned and discount offered also motivated me to sign up.
Course Registration
The course is available for 30, 60 and 90 days – I chose 60. This enabled me to just take my time studying the course content in the evening after work. Once I applied for registration I had the option of either starting immediately or within 90 days. I chose to start a few weeks later. On my course start date I received links to download the course material and vpn connection details. I was also provided with a dedicated windows virtual machine.
Course Prerequisites
The prerequisites for this course as stated on the course page are:
- Basic understanding of Active Directory
- Ability to use command line tools on Windows
I was already well versed in the two topics above so I had no problems signing up. However if you feel like you need some experience what I can recommend is setting up an AD lab and practicing some attacks on your own. There’s an excellent resource which you can use to build your AD lab by Jared Haight. After that you can recreate attack scenarios following blogs such as https://adsecurity.org, http://blog.harmj0y.net and other blogs on AD. Those two blogs are the ones that I used the most in the Labs.
A Word on Note Taking
I learnt from taking OSCP that taking clear, thorough and reproducible notes are a key to success. The course content is a lot of material and I was glad I had all my notes handy and in an easily searchable format. I used CherryTree with four backups, synced the files with Dropbox and also saved them to an external hard disk. I used to back up after every learning session was done each night. This proved to be invaluable when documenting and writing my final exam report.
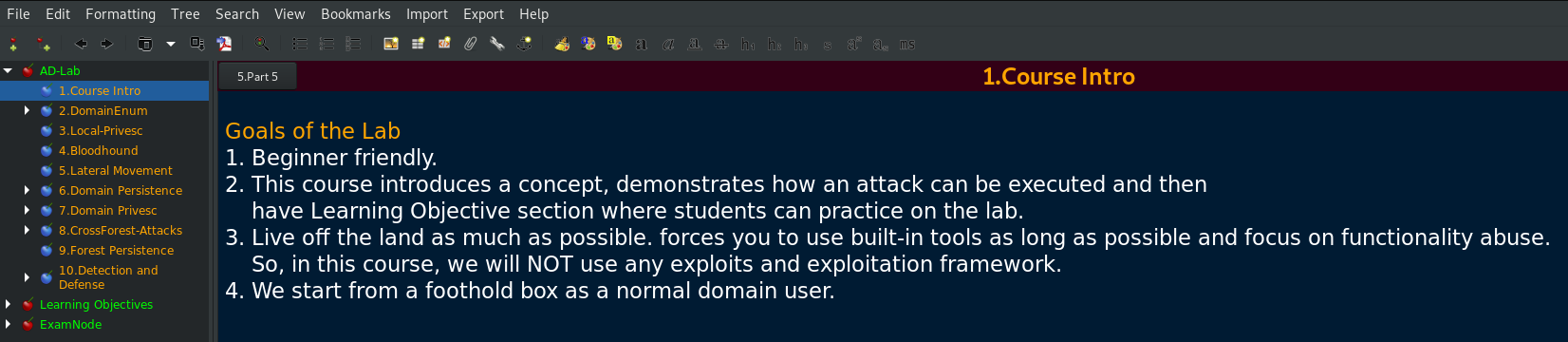
Course Overview
There are three components to the course. The learning material which includes several hours of videos and accompanying PDFs is the first. My approach was to go chapter by chapter watching the videos along with the course PDF guide. I personally consider the course content to be of very high quality.
The second is performing the related learning tasks in the Lab to let the material sink in. I could tell the author spent countless hours designing and developing the course content to go hand in hand with the Labs. The content covers ten subjects followed by 23 learning objectives. The content is well thought out and structured. This enabled me to easily follow, understand and recreate attack steps in every attack covered. The ten subjects are:
- Active Directory Enumeration
- Local Privilege Escalation
- Domain Privilege Escalation
- Domain Persistence and Dominance
- Cross Trust Attacks
- Forest Persistence and Dominance
- Defenses – Monitoring
- Defenses and Bypass – Deception
- Defenses and Bypass – PowerShell
The third and final section of the course was the exam.
The Exam
After I managed to go through the course material several times, I felt confident enough to sign up for the exam. The exam is 24 hours in a separate AD forest. The goal of the exam is to gain command execution on target systems with any privilege. The exam required me to go into my bag of tricks learnt during the course to eventually come out victorious. After the exam time had expired, I had 48 hours to write a detailed report and submit it. The report contained a detailed walk-through of my approach to compromise a box with screenshots, tools used and their outputs. The report also contained practical recommendations for the misconfigurations which were exploited to gain access to the systems.
Certification
After about a day or so after submitting the report, I received an email saying I had passed the certification. They also gave me a shout-out on twitter.
Conclusion
I highly recommend this course to anyone who wants to improve their knowledge with regards to Active Directory Attacks and Defense. I learned a lot and I can’t recommend it enough for anyone that wants to wants to get access to a quality lab environment and hone their AD skills.
A day later, I got a personal email from the course author Nikhil Mittal thanking me for a well accomplished exam, writing a great report and a job well done. I was then able to provide detailed feedback on what I liked during the course and what could be improved upon to enhance the student experience. He even took the time to reply to my recommendations during his busy BruCon class. It showed the commitment Nikhil Mittal has to genuinely hear their students out and improve the labs for future students.
Also great thanks to Pentester Academy who provided great support during the lab and the exam. Special thanks to Nikhil Mittal and Pentester Academy for creating and hosting an awesome course.
Feel free to message me on twitter with any questions.